Psiphon
Making privacy easier with Psiphon
(An illustrated explanation)

When it comes to evading Internet censorship and spying, sometimes it’s not what but who you know and trust. Psiphon offers VPN-like security and encryption built on top of a closed, trusted network.
Once you have a Psiphon account, you can log in through a network of proxy servers to connect to the main Psiphon server.
*Psiphon supports Windows and Android.
Psiphon is a fairly robust circumvention tool that provides some, but not complete, privacy protection.
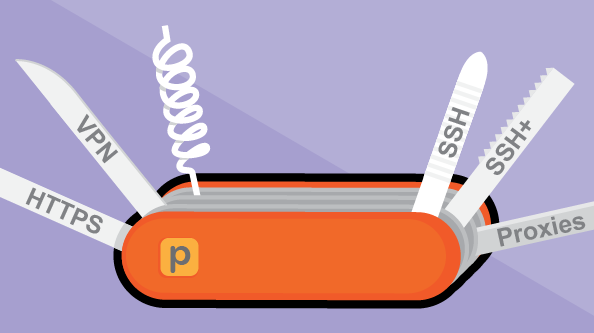
It employs a variety of tools to evade censorship.
On a Windows PC:

The user downloads a small executable file.
Psiphon will attempt to find a connection through an available proxy server.

Users can connect with SSH, SSH+ or VPN.

Psiphon even offers an option to route international traffic through proxies while domestic sites aren't.
On an Android device:

When a user launches the Psiphon app, it will automatically start connecting to the Psiphon network.

By default, only the Psiphon browser is tunneled through the Psiphon network.

Users with Android 4.0+ or a rooted phone may tunnel other browser and app traffic through Psiphon.
Tunnel whole device
What Is Psiphon?
Psiphon was created by the Internet-freedom center “Citizen Lab” at the University of Toronto, before being handed off to a private group for management and upkeep, funded in part by VOA’s parent agency, the Broadcasting Board of Governors.
First released in 2006, Psiphon offers VPN-like security and encryption in a fast, easy-to-use design. Unlike tools such as Tor or PGP, Psiphon employs a variety of technical tricks (HTTPS, SSH+, proxy servers and others) rather than one specific design to help users evade online censorship.
There are currently two supported versions: Psiphon2 and Psiphon3. It’s important to note they work very differently: Psiphon2 is a web proxy that works inside your browser window, while Psiphon3 is an executable file that provides a more complete browsing experience. You can learn more about the differences at Psiphon.ca; here we’ll be looking at the more popular Psiphon3.
How Psiphon works
Each successive version of Psiphon has become easier to use, and the latest version – Psiphon3 – requires only a small amount of resources on the user’s device.
It works like this: Psiphon3 is a native application that lives on a user’s computer. Prospective users only need to download the application and open it on their device. Remember: Psiphon does not store any user information or activity on their servers, creating an extra layer of privacy.
Psiphon3 downloads as an executable file (.exe) that is digitally signed by Psiphon. This security signature allows your operating system to certify the file you’ve downloaded is actually the correct Psiphon application, avoiding malicious look-alikes. More sophisticated users can even inspect the specifics of the digital authentication.
When a user clicks “run,” the file automatically attempts to connect to the distributed network of Psiphon servers. Once connected the client window opens in a browser. Users can then choose how they want to use Psiphon3. When the “VPN mode” is disabled, only applications that use HTTPS will be protected; when “VPN mode” is turned on, all data traffic on your device will be tunneled.
How can Psiphon help me?
Psiphon3 is a fairly robust circumvention tool and provides some, but not complete, privacy protection and robust circumvention.
Let’s say you want to visit Facebook, but that site is blocked in your country. When you launch Psiphon3 and are connected to the network, an encrypted tunnel is created between your device. It’s not guaranteed – nothing is – but it can make accessing banned websites much easier.
Possible drawbacks
There are two major drawbacks. First, Psiphon is only designed to work on Windows and Android systems, putting it out of reach for Apple or other OS systems.
Second, because Psiphon3 only lives on your individual device, it is not useful for users who frequent cyber cafes, or use devices that other members of the public can also access. Additionally, Psiphon3 is not a multi-purpose total anonymizing tool like Tor that can be used in a variety of settings. Users seeking privacy protection or anonymization should look to other tools that, if desired, can be used alongside Psiphon3.
While traffic routed within the Psiphon network is encrypted, there’s nothing stopping anyone from detecting that your computer is connected to a known Psiphon server. Additionally, those Psiphon servers, while constantly changing, do not protect against outside traffic analysis, meaning that with sophisticated tools, a government could probe to detect the users’ identity and any unencrypted traffic flowing through the server. That said, all traffic is encrypted between the end user and the Psiphon server they connect to.
Some analysts have also speculated that Psiphon’s particular design could make it vulnerable to man-in-the-middle attacks. In such attacks, a hidden user can access the secure information flowing between two points on the Internet, making it look like a secure connection but in actuality intercepting the data flows. This is not unique to Psiphon, but something to keep in mind.
The bottom line
Psiphon has proven to be a fairly robust tool to evade government censorship and, to a lesser degree, protect your privacy. It’s easy to use, and because it lives on your Windows computer or Android mobile device, you can always have it at hand in the privacy of your home.